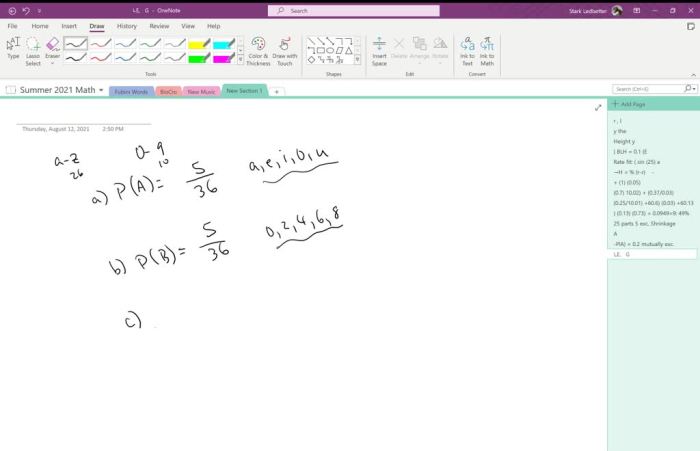
A computer system uses passwords that are six characters – A computer system’s use of passwords that are six characters in length raises important considerations regarding security and effectiveness. This article will delve into the complexities of password management, exploring the relationship between password length and security, examining various password storage methods, and discussing the importance of password policies.
By understanding these concepts, organizations can implement robust password management practices that protect their systems and data from unauthorized access.
Password Complexity
Password complexity is essential for enhancing the security of computer systems. Complex passwords are more challenging to guess or crack, making them less vulnerable to unauthorized access.
Examples of complex passwords include those that contain a combination of uppercase and lowercase letters, numbers, and special characters. Additionally, passwords should be at least 12 characters long and avoid common words or phrases that can be easily guessed.
Benefits of Using Complex Passwords
- Increased resistance to brute-force attacks
- Reduced likelihood of successful password guessing
- Enhanced protection against phishing and social engineering attempts
Password Length: A Computer System Uses Passwords That Are Six Characters
Password length plays a crucial role in password security. Longer passwords are more difficult to crack, as they increase the number of possible combinations that an attacker would need to guess.
Studies have shown that passwords with a minimum length of 12 characters are significantly more secure than shorter passwords. For optimal security, passwords should be at least 15 characters long.
Optimal Password Length for Computer Systems
The optimal password length for computer systems is a balance between security and usability. Passwords that are too long may be difficult for users to remember, while passwords that are too short may be more vulnerable to attack.
Password Storage
Proper password storage is essential for protecting user credentials from unauthorized access. There are various methods for storing passwords, each with its own security implications.
Methods for Storing Passwords, A computer system uses passwords that are six characters
- Plaintext storage: Passwords are stored in their original, unencrypted form.
- Hashing: Passwords are converted into a one-way hash function, making them difficult to recover.
- Salting: A random value is added to the password before hashing, further increasing security.
Security of Password Storage Methods
Salting is the most secure method for storing passwords, as it prevents attackers from using pre-computed hash tables to crack passwords.
Password Management
Password management tools assist users in generating, storing, and organizing their passwords securely.
Benefits of Using a Password Manager
- Centralized storage of passwords, eliminating the need to remember multiple passwords
- Automatic generation of strong and complex passwords
- Secure synchronization of passwords across multiple devices
Examples of Password Management Tools
- LastPass
- 1Password
- Dashlane
Effective Use of Password Managers
- Use a strong master password to protect the password manager
- Enable two-factor authentication for added security
- Regularly review and update stored passwords
Password Reset
Password reset procedures allow users to regain access to their accounts when they have forgotten or lost their passwords.
Methods for Resetting Passwords
- Security questions: Users answer pre-defined security questions to verify their identity.
- Email or SMS verification: A one-time password is sent to the user’s registered email address or phone number.
- Password reset token: A unique token is generated and sent to the user, allowing them to reset their password without answering security questions.
Importance of Secure Password Reset Procedures
Secure password reset procedures are essential to prevent unauthorized individuals from gaining access to user accounts.
Password Cracking
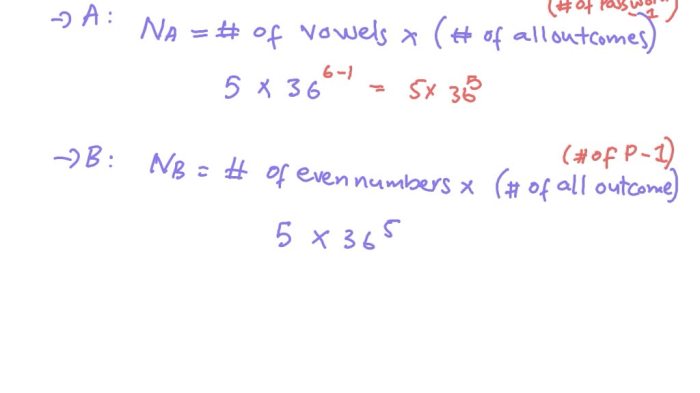
Password cracking refers to the process of recovering passwords from encrypted or hashed storage.
Methods for Cracking Passwords
- Brute-force attacks: Iteratively trying all possible combinations of characters
- Dictionary attacks: Using a list of common words and phrases to guess passwords
- Rainbow tables: Pre-computed tables that map hashed passwords to their plaintext equivalents
Effectiveness of Password Cracking Methods
The effectiveness of password cracking methods depends on the complexity and length of the password.
Preventing Password Cracking
- Use strong and complex passwords
- Implement salting and hashing algorithms
- Enforce password aging policies
Password Policies
Password policies define the rules and guidelines for creating and managing passwords.
Importance of Password Policies
Password policies help organizations enforce password security standards and reduce the risk of unauthorized access.
Effective Password Policies
- Minimum password length requirements
- Complexity requirements (uppercase, lowercase, numbers, special characters)
- Regular password expiration and reset schedules
- Prohibition of common and easily guessable passwords
Best Practices for Implementing Password Policies
- Communicate password policies clearly to users
- Provide training on password security
- Enforce password policies consistently
User Queries
What is the optimal password length for a computer system?
While there is no definitive answer, experts generally recommend using passwords that are at least 12 characters long.
What is the most secure method for storing passwords?
The most secure method for storing passwords is using a password manager that utilizes strong encryption and multi-factor authentication.
What is a password policy?
A password policy is a set of rules that define the requirements for creating and using passwords within an organization.